BlueTooth Low Energy
This blog is used to conclude the BLE main knowleadge point in my working life.
Bluetooth Core System Architecture
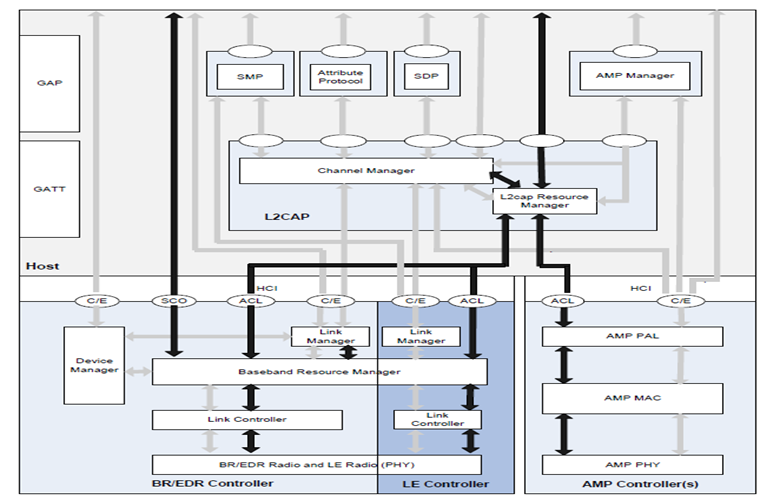 </img>
</img>
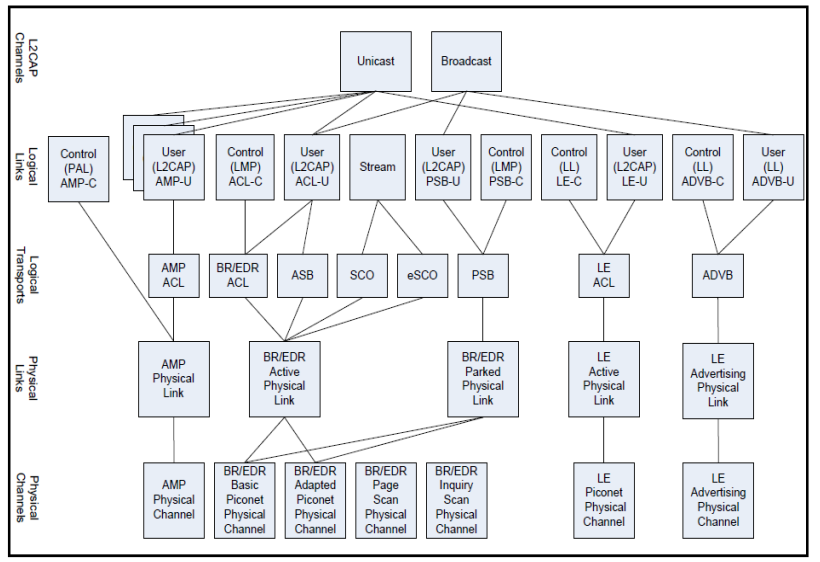 </img>
</img>
BLE PHY
-
BLE channel numbter:37, index at 0~36
-
BLE broadcast channel:3, index at 37,38, 39
- BLE channel frequency range:2402~2480MHz
- BLE channel bandwidth: 2MHz
BLE 网络中主(Master)和Slave(从)设备的数据基本交互方式如下:
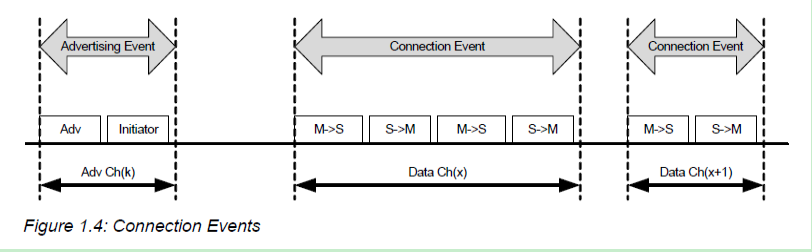 </img>
</img>
Broadcast channel
During broadcast, including 3 roles:
-
advertiser
transimit advertising packet -
scanner
receiving advertising packet but don’t intension to establish connection -
initiator
listen advertising packet and intend to initialize an link
Physical link
- LE active physical link
- LE advertising physical link
Logic transport
BLE Roles & message exchange procedure
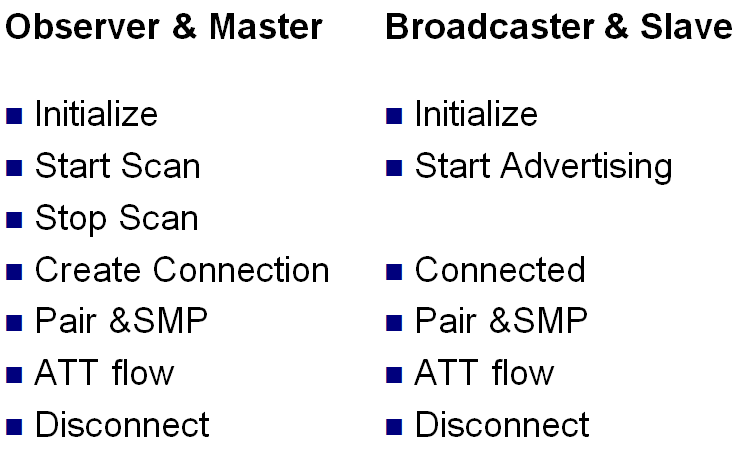 </img>
</img>
Device Address
-
BD_ADDR(48bit: lower-24bit, upper-8bit)
-
AM_ADDR(3bit): master allocte for slave when slave at the state of active to identify different slave device.
-
PM_ADDR(8bit): when device transit state from active to park, allocated with this kind of address.
-
AR_ADDR: device at the state of park use this address to request to master to transit the state to active , and the same address can be used by more than one device;
Link layer
Security Manager
Security manager position in BLE stack

SMP procedure analysis
Defines the protocol and behavior to manage pairing, authentication and encryption between LE devices.
- Authentication and key management
- AES-128
- Secure link
Pair phase including 4 phases:
- Phase 1: Pairing Feature Exchange
- Phase 2 (LE legacy pairing): Short Term Key (STK) Generation
- Phase 2 (LE Secure Connections): Long Term Key (LTK) Generation (optional)
- Phase 3: Transport Specific Key Distribution

In phase 1, authenticatioin requirement and IO capability will be exchanged, and the following method will be determined and used in Phase2:
- Just Works
- Numeric Comparison (Only for LE Secure Connections)
- Passkey Entry
- Out Of Band (OOB)
and here, list the IO capability defined in spec, as below:

And OOB Authentication Data is descriped as below:
An out of band mechanism may be used to communicate information which is used during the pairing process. The information shall be a sequence of Advertising Data structures
In LE legacy pairing, the out of band method is used if both the devices have the other device’s out of band authentication data available. In LE Secure Connections pairing, the out of band method is used if at least one device has the peer device’s out of band authentication data available.
the Out of Band method can be more secure than using the Passkey Entry or Just Works methods.
L2CAP analysis

L2CAP function:
-
Protocol/channel multiplexing
-
Segmentation and reassembly
-
Flow control per L2CAP channel:A window based flow control scheme is provided
-
Error control and retransmissions
-
Support for Streaming: AUDIO (BR/EDR),not BLE
-
Fragmentation and Recombination(seem common function with “segmentation”)
-
Quality of Service
BLE packet format
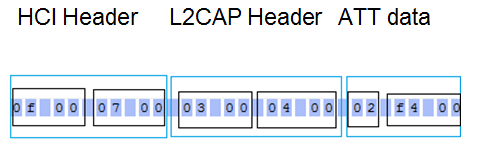 </img>
</img>
HCI Header: Handle (2Bytes) + Length (2Bytes)
L2CAP Header: PDU Length (2 Bytes) + CID(2Bytes)
ATT Data: Opcode (1Byte) + Data(variable)
Packet type
Four logical transports with distinct packet types are defined:
-
SCO logical transport
-
eSCO logical transport
-
ACL logical transport
-
CSB logical transport.
To indicate the different packets on a logical transport, the 4-bit TYPE code is used,The packet types are divided into four segments:

- The first segment is reserved for control packets. All control packets occupy a single time slot.
- The sec- ond segment is reserved for packets occupying a single time slot.
- The third seg- ment is reserved for packets occupying three time slots.
- The fourth segment is reserved for packets occupying five time slots. The slot occupancy is reflected in the segmentation and can directly be derived from the type code. Table 6.2 on page 125 summarizes the packets defined for the SCO, eSCO, ACL, and CSB logical transport types.
GATT & ATT
GATT hierarchy:

GATT procedure
Here, List whole GATT procedure as belows:


